HAPPY NEW YEAR
DO IT DAILY
Turn your smart phone off every day. Wait a few minutes – or a few hours – whatever works best for you – then restart it. This ensures everything is up to date and working properly. We solve peoples’ smart phone problems in this way several times every week.
Very Useful Tech Tool
 I’m referring to the Sandisk iXpand™ Mini Flash Drive for iPhone & iPad. Capacity: 64 GB • Interface: Lightning™ Connector and USB 3.0. The iXpand Mini Flash Drive is an easy-to-use storage device for those with an iPad or iPhone that needs some extra storage space – or backup. Herein, we’ll focus on phone use, but iPad use doesn’t vary much at all. In order to use this device, which you merely plug-in to your iPhone where the charger plugs in, you’ll need the iXpand Drive app – which is free. When you first plug-in, you’ll be prompted to get the app, which downloads very fast and is super-easy to use. The iXpand Drive app makes it easy to manage photos and videos, watch videos directly from the drive, and even take videos from the app and save them directly onto the drive. The Apple connector is on one side, and on the other side is a USB 3.0 female – so you can plug it into your computer. While Sandisk makes several similar devices, this is the only one I’ve bought and used – and would recommend. I was prompted to spend the $34.99 on the 64Gb model (it’s also available in a 32Gb and 128Gb models) because of Apple’s coming price increase for using their iCloud storage. I know a lot of clients keep oodles of family photos on their phones – and phone storage is pricey, and the cloud is about to become more costly. That being said, download family photos to this unit and back them up on a WD SSD, such as the 1Tb Passport model for about $299. Now you’ve got lifetime storage with no moving parts – of an entire Tb – that’s about 16 FULL 64Gb Sandisk iXpand™ Mini Flash Drive loads of files. See more about this device by clicking here.
I’m referring to the Sandisk iXpand™ Mini Flash Drive for iPhone & iPad. Capacity: 64 GB • Interface: Lightning™ Connector and USB 3.0. The iXpand Mini Flash Drive is an easy-to-use storage device for those with an iPad or iPhone that needs some extra storage space – or backup. Herein, we’ll focus on phone use, but iPad use doesn’t vary much at all. In order to use this device, which you merely plug-in to your iPhone where the charger plugs in, you’ll need the iXpand Drive app – which is free. When you first plug-in, you’ll be prompted to get the app, which downloads very fast and is super-easy to use. The iXpand Drive app makes it easy to manage photos and videos, watch videos directly from the drive, and even take videos from the app and save them directly onto the drive. The Apple connector is on one side, and on the other side is a USB 3.0 female – so you can plug it into your computer. While Sandisk makes several similar devices, this is the only one I’ve bought and used – and would recommend. I was prompted to spend the $34.99 on the 64Gb model (it’s also available in a 32Gb and 128Gb models) because of Apple’s coming price increase for using their iCloud storage. I know a lot of clients keep oodles of family photos on their phones – and phone storage is pricey, and the cloud is about to become more costly. That being said, download family photos to this unit and back them up on a WD SSD, such as the 1Tb Passport model for about $299. Now you’ve got lifetime storage with no moving parts – of an entire Tb – that’s about 16 FULL 64Gb Sandisk iXpand™ Mini Flash Drive loads of files. See more about this device by clicking here.
Politech
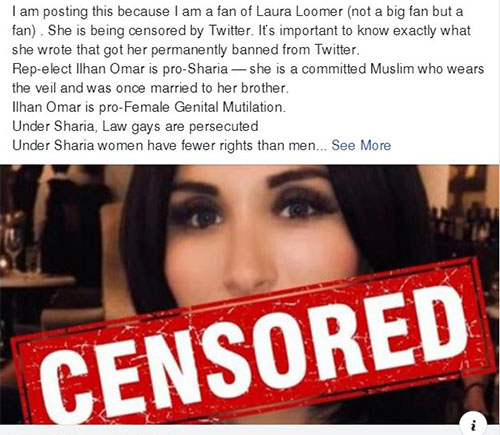
 That’s my new word. It means combining technology and politics. I use it here because what I am about to say enters into both realms. On November 27th, I cancelled all my Twitter accounts: 2 were for personal businesses and 11 were for client businesses. I also notified those clients that I will no longer be using Twitter in any marketing programs. I would have preferred not to take these actions, if for no other reason than the substantial loss of income to Luci’s Office. However, Twitter has taken upon itself to decide what [free] speech is acceptable, and what is not. Needless to say, that is hardly “free” speech, and in my opinion, Twitter has been utterly irresponsible and abusive with that power. Ironically, the straw that broke this camel’s back was when a person I wholly disagree with was banned from Twitter for expressing their opinion. While I disagree with them, they were not hateful, and made what they considered to be relevant arguments in a fairly intelligent manner. Twitter literally changed their rules (ex post facto) specifically to delete this woman’s account. This is not right. This is not fair. This is un-American. BTW – I am very close to taking similar actions with FaceBook. I have not done it because I believe it would be too detrimental to my clients’ businesses. Below, I’ve posted just one example (screen clipping) of their censorship. Following are the easy instructions to deactivate your Twitter account:
That’s my new word. It means combining technology and politics. I use it here because what I am about to say enters into both realms. On November 27th, I cancelled all my Twitter accounts: 2 were for personal businesses and 11 were for client businesses. I also notified those clients that I will no longer be using Twitter in any marketing programs. I would have preferred not to take these actions, if for no other reason than the substantial loss of income to Luci’s Office. However, Twitter has taken upon itself to decide what [free] speech is acceptable, and what is not. Needless to say, that is hardly “free” speech, and in my opinion, Twitter has been utterly irresponsible and abusive with that power. Ironically, the straw that broke this camel’s back was when a person I wholly disagree with was banned from Twitter for expressing their opinion. While I disagree with them, they were not hateful, and made what they considered to be relevant arguments in a fairly intelligent manner. Twitter literally changed their rules (ex post facto) specifically to delete this woman’s account. This is not right. This is not fair. This is un-American. BTW – I am very close to taking similar actions with FaceBook. I have not done it because I believe it would be too detrimental to my clients’ businesses. Below, I’ve posted just one example (screen clipping) of their censorship. Following are the easy instructions to deactivate your Twitter account:
- Log in to Twitter.
- Click on your profile image in the upper-right corner of the window.
- Click on Settings and privacy.
- Scroll down and click on Deactivate my account.
- Click on Deactivate
- Enter your Twitter password.
Bottom line: in my opinion, social media cannot be allowed to become the governing body over free speech. Granted, free speech comes with responsibilities, but Americans must exercise those discretionary parameters on an individual basis – which often depend on audience and circumstance. You should know that abandoning Twitter puts you into a very large group of folks who have recently seen what’s happening and have left the service. Excuse me while I now jump down off my soap box…
I’m Not Leaving You High & Dry!
 There is a service similar to Twitter, but without the biased oversight, that is growing like a weed: gab. Their slogan is A social network that champions free speech, individual liberty and the free flow of information online. All are welcome. Join them by clicking here. I hope to see your posts soon! Oh, and please tell your friends to signup also.
There is a service similar to Twitter, but without the biased oversight, that is growing like a weed: gab. Their slogan is A social network that champions free speech, individual liberty and the free flow of information online. All are welcome. Join them by clicking here. I hope to see your posts soon! Oh, and please tell your friends to signup also.
Free is Attractive, But!
 Some free services are mostly harmless. They make their money by splashing ads around and through whatever they are giving you. Some free services are actually teasers, and are provided with the hope that you’ll buy the service, product, whatever. In the world of VPNs, free is not really a very good or safe choice. I’ll start the rest of this article by saying if you really want a free VPN, go with TunnelBear. They cap your use to 500Mb per month, but they’re safe – the 500Mb is the teaser. Okay, some of you may not know what a VPN is, so here’s a quick, simple explanation: VPN stand for virtual private network. When you go online, your commands are encrypted and sent to the VPN, which then forwards them, receives the response and encrypts it and then sends it back to your device. This prevents whoever you contacted from knowing who or where you are – with one exception: the VPN owner. Example: you sit down at your computer in Miles City, MT open your browser and ask DuckDuckGo ‘how to make a quilt?’ The screen quickly fills with answers. You click the answer you like best: Marybeth Johnson’s Home Guide to Quilt Making. You enter her site, get the data you want, and leave. Her servers have no idea who you are, what system you’re using, where you are located – or anything else about you. Her servers may think you’re in Cairo, Egypt. VPNs make superb insulators and provide robust anonymity. I should say “good” VPNs. Bottom line: if you’re thinking the anonymity and safety of a VPN is right for you, go ahead and buy one like TunnelBear, which is $9.99 per month for unlimited data. At the top of the VPN food chain there’s ExpressVPN – costs vary on this last one, but it’s very powerful and very safe. NB ExpressVPN is the one we use.
Some free services are mostly harmless. They make their money by splashing ads around and through whatever they are giving you. Some free services are actually teasers, and are provided with the hope that you’ll buy the service, product, whatever. In the world of VPNs, free is not really a very good or safe choice. I’ll start the rest of this article by saying if you really want a free VPN, go with TunnelBear. They cap your use to 500Mb per month, but they’re safe – the 500Mb is the teaser. Okay, some of you may not know what a VPN is, so here’s a quick, simple explanation: VPN stand for virtual private network. When you go online, your commands are encrypted and sent to the VPN, which then forwards them, receives the response and encrypts it and then sends it back to your device. This prevents whoever you contacted from knowing who or where you are – with one exception: the VPN owner. Example: you sit down at your computer in Miles City, MT open your browser and ask DuckDuckGo ‘how to make a quilt?’ The screen quickly fills with answers. You click the answer you like best: Marybeth Johnson’s Home Guide to Quilt Making. You enter her site, get the data you want, and leave. Her servers have no idea who you are, what system you’re using, where you are located – or anything else about you. Her servers may think you’re in Cairo, Egypt. VPNs make superb insulators and provide robust anonymity. I should say “good” VPNs. Bottom line: if you’re thinking the anonymity and safety of a VPN is right for you, go ahead and buy one like TunnelBear, which is $9.99 per month for unlimited data. At the top of the VPN food chain there’s ExpressVPN – costs vary on this last one, but it’s very powerful and very safe. NB ExpressVPN is the one we use.
Phishing Attacks in a Nutshell
Phishing is the term used to describe the deceitful means used to obtain an individual’s or company’s crucial/private information. Phishing scams are rampant. And sadly, it’s because they all-too-often work. The information sought includes:
- Phone Numbers
- Usernames
- Emails
- Social Security Numbers
- Passwords
- Credit Card Details
- Bank Account Information
- Addresses
- Answers to “Secret Questions” (used for verification)
In typical phishing schemes, the intended victim is baited with an email from an entity that is pretending to be trustworthy. Of course, not all such companies/entities can be listed, but they include:
- Retail Companies
- Popular Online Shopping Sites
- Banks
- Electronic Communicators
- Internet Providers
- Local Shops
- The IRS
- The Social Security Administration
- Health Insurance Carriers
 Do NOT send or offer to send your information in response to emails unless you are absolutely, positively, beyond any shadow of any doubt sure of who is getting it. Add a layer of security by getting a phone number and calling the inquirer – especially banks and government organizations. When you send login info to friends and family, which is quite often done, do it in segments via different devices. If you want your child to have your bank sign-in info, try this:
Do NOT send or offer to send your information in response to emails unless you are absolutely, positively, beyond any shadow of any doubt sure of who is getting it. Add a layer of security by getting a phone number and calling the inquirer – especially banks and government organizations. When you send login info to friends and family, which is quite often done, do it in segments via different devices. If you want your child to have your bank sign-in info, try this:
- Send just the email address used via email – with no other info attached.
- Then TEXT the security question answers ONLY – with no other info attached.
- Then call and TELL them the password verbally.
- If you need to send other relevant info, put it into a notepad and attach it to an email.
Remember – emails are frequently read by machines, and sometimes by people. Be secure and be safe. NB if you use WORD, you can encrypt a file and make it require a password to be opened – great way to send sensitive data as an attachment.
Unfollow on Facebook
If you find yourself deluged with comments from friends, or information you really don’t want to see anymore, you can simply unfollow people. It’s easy: When you come upon a post from someone you don’t always need to here every excruciating bit of minutia from, click the three dots at the top right of the post and select the “Unfollow (Person)” option. Voila!
This is Going to Get Complicated
I am going to pre-apologize for the length and complexity of the following, but it’s quite important that you have the information. Not following a proper protocol for your Windows 10 updates could cause your system to fail or not function properly. So, let’s get started… NB Spoiler Alert: I’ll end this article with a simple instruction to keep you safe.
 Microsoft has announced that there will now be updates designated B, C and D. These updates will not all come at once, nor will they be distributed universally.
Microsoft has announced that there will now be updates designated B, C and D. These updates will not all come at once, nor will they be distributed universally.
- About every 6-months Microsoft releases a very large and important update.
- The C and D updates mentioned above will be called “quality updates,” and only distributed during each month. The name is intended to convey that the update is cumulative and repairs bugs from previous versions.
- B-updates are put out in the 2nd week of the month, and they contain the most necessary updates.
- C-updates come in the 3rd week of the month and D-updates come in the 4th week.
Are you with me so far? Good – ‘cause now it gets whacky, compliments of Microsoft…
Your Windows Update doesn’t automatically install the C-updates and the D-updates on most PCs. However, it will install both C and D updates if you navigate over to Settings > Update & Security > Windows Update and click on Check for Updates. When you do this, you automatically become a Microsoft “seeker.” That means YOU want to test these updates before other users receive them.
Ergo, if you do navigate to (and click) Check for Updates in the 1st, 3rd or 4th week of a month before the newest B update has been fully tested and released, you can expect to become an unwitting seeker who receives a C and/or D update installed on your computer. These updates are not fully tested and might cause you to have some wholly undesirable issues.
Bottom Line: NEVER click “Check for Updates!” Stay with the fully tested B-updates.